8.1 Firewall management tools
May 23, 2021 That's what Linux should learn
As we all know, compared with the enterprise intranet, the external public network environment is more bad, full of evil. F irewalls that act as a protective barrier between the public and enterprise intranets (see Figure 8-1) although there is software or hardware, the main function is to filter traffic through the firewall itself according to policy. F irewall policies can be customized based on information such as the source address, port number, protocol, application, etc. of traffic, and then the firewall uses pre-customized policy rules to monitor traffic in and out, and if the traffic matches a policy rule, the appropriate processing is performed and discarded. In this way, only legitimate traffic can be guaranteed to flow between the enterprise intranet and the external public network.
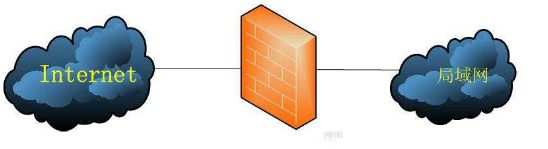
Figure 8-1 Firewall serves as a protective barrier between the public and intranets
In the RHEL 7 system, the firewalld firewall replaces the iptables firewall. F or readers who have been exposed to Linux systems earlier or who have learned the RHEL 6 system, there is bound to be resistance when they find that the knowledge they once mastered no longer applies in RHEL 7 and that new learning of firewalld is required. I n fact, neither iptables nor Firewalld are real firewalls, they are just firewall management tools used to define firewall policies, or they are just a service. T he iptables service leaves the configured firewall policy to the kernel-level netfilter network filter, while the firewalld service leaves the configured firewall policy to the kernel-level nftables package filtering framework. I n other words, there are currently multiple firewall management tools in Linux systems designed to make it easier for operations personnel to manage firewall policies in Linux systems, and we just need to configure one of them properly. A lthough these tools have their advantages and disadvantages, they are consistent in the configuration of firewall policies. You don't even have to fully grasp the contents of this chapter, as long as you choose one of these firewall management tools and learn through it, it is enough to meet the daily needs of the work.