16.3.2 ACL access control
May 24, 2021 That's what Linux should learn
In the daily work, enterprise employees generally access the Internet through the company's internal gateway server, when the Squid service program is deployed as the gateway server of the corporate network, the Squid service program access control list (ACL) function will play its role. I t can cache data or restrict user access based on specified policy criteria. F or example, many companies will ban employees from visiting Taobao, playing web games, these prohibitions can be achieved through the ACL function of the Squid service program. If you later engage in operations and operations in a company with a large turnover of people, you can keep in mind this section, add certain policy conditions to the Squid service program deployed on your company's gateway servers, and prevent employees from accessing certain recruitment sites or competitors' websites, which may also effectively reduce employee churn.
The ACL of the Squid service program consists of multiple policy rules that allow or restrict access requests based on the specified policy rules, and the policy rules are matched in the same order as firewall policy rules from top to bottom; To prevent the ACL from banning all traffic or releasing it al completely, with less than expected access control effects, operations personnel typically write a deny all or all statement at the bottom of the ACL to avoid security risks.
Through the following 4 experiments, Mr. Liu will demonstrate how powerful the ACL of the Squid service program is.
Lab 1: Only clients with IP addresses of 192.168.10.20 are allowed to use the proxy services provided by the Squid service program on the server, and all remaining host agent requests are prohibited.
The following profile is still the profile of the Squid service provider, but you need to pay attention to where the configuration parameters are filled in. I f you write too far ahead, some Squid service providers do not load their own statements, which can also cause the policy to be invalid. Of course, also do not need to be too far back, about 26 to 32 lines can be located, and the use of branch filling method is also easy to modify later.
[root@linuxprobe ~]# vim /etc/squid/squid.conf 1 # 2 # Recommended minimum configuration: 3 # 4 5 # Example rule allowing access from your local networks. 6 # Adapt to list your (internal) IP networks from where browsing 7 # should be allowed 8 acl localnet src 10.0.0.0/8 # RFC1918 possible internal network 9 acl localnet src 172.16.0.0/12 # RFC1918 possible internal network 10 acl localnet src 192.168.0.0/16 # RFC1918 possible internal network 11 acl localnet src fc00::/7 # RFC 4193 local private network range 12 acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) mac hines 13 14 acl SSL_ports port 443 15 acl Safe_ports port 80 # http 16 acl Safe_ports port 21 # ftp 17 acl Safe_ports port 443 # https 18 ac l Safe_ports port 70 # gopher 19 acl Safe_ports port 210 # wais 20 acl Safe_ports port 1025-65535 # unregistered ports 21 acl Safe_ports port 280 # http-mgmt 22 acl Safe_ports port 488 # gss-http 23 acl Safe_ports port 591 # filemaker 24 acl Safe_ports port 777 # multiling http 25 acl CONNECT method CONNECT 26 acl client src 192.168.10.20 27 # 28 # Recommended minimum Access Permission c onfiguration: 29 # 30 # Deny requests to certain unsafe ports 31 http_access allow client 32 http_access deny all 33 http_access deny ! S afe_ports the configuration parameters root@linuxprobe on the systemctl restart squid are actually easy to understand. F irst, an alias named is defined. T his is similar to the DNS separation parsing technique explained in Section 13.6, when we defined two alias variables called china and american, so that when we encounter the alias again, we mean the IP address defined with it. After saving the profile and restarting the Squid service program, the client host is prohibited from using the proxy service because its IP address does not comply with our allowed policy, as shown in Figure 16-8.
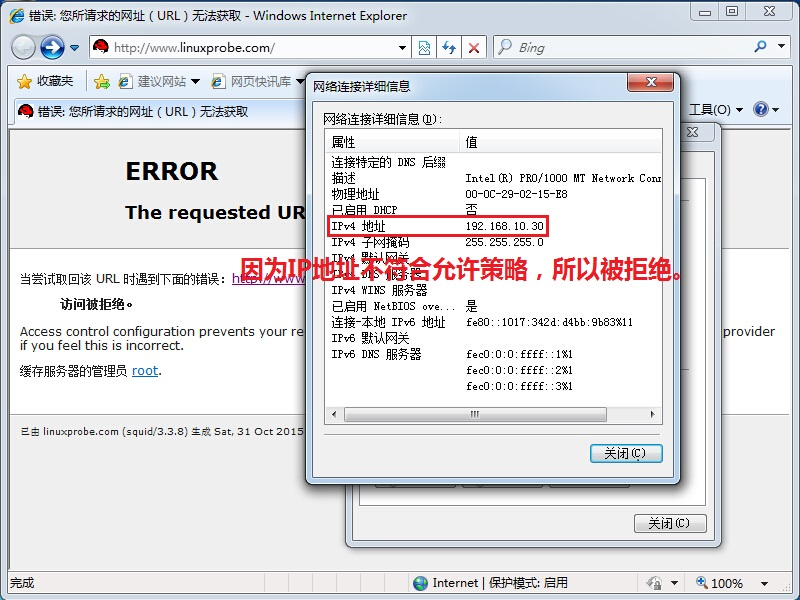
Figure 16-8 Failed to browse the web using the proxy service
Lab 2: All clients are prohibited from accessing websites with linux keywords in their URLs.
This ACL functionality pattern of the Squid service program is crude and violent, and any URL accessed by the client that contains a keyword is immediately blocked, but this does not affect access to other websites.
[root@linuxprobe ~]# vim /etc/squid/squid.conf 1 # 2 # Recommended minimum configuration: 3 # 4 5 # Example rule allowing access from your local networks. 6 # Adapt to list your (internal) IP networks from where browsing 7 # should be allowed 8 acl localnet src 10.0.0.0/8 # RFC1918 possible internal network 9 acl localnet src 172.16.0.0/12 # RFC1918 possible internal network 10 acl localnet src 192.168.0.0/16 # RFC1918 possible internal network 11 acl localnet src fc00::/7 # RFC 4193 local private network range 12 acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) mac hines 13 14 acl SSL_ports port 443 15 acl Safe_ports port 80 # http 16 acl Safe_ports port 21 # ftp 17 acl Safe_ports port 443 # https 18 acl Safe_po rts port 70 # gopher 19 acl Safe_ports port 210 # wais 20 acl Safe_ports port 1025-65535 # unregistered ports 21 acl Safe_ports port 280 # http-mgmt 22 acl Safe_ports port 488 # gss-http 23 acl Safe_ports port 591 # filemaker 24 acl Safe_ports port 777 # multiling http 25 acl CONNECT method CONNECT 26 acl deny_keyword url_regex -i linux 27 # 28 # Recommended minimum Access Permission configuration : 29 # 30 # Deny requests to certain unsafe ports 31 http_access deny deny_keyword 33 http_access deny ! S afe_ports 34 (root@linuxprobe) - The systemctl restart squid suggests that you clean up the code from the previous experiment before you do it, so as not to conflict between different experiments. I n the current experiment, we directly defined an alias called deny_keyword, and then rejected all web site requests with linux keywords. When clients visit sites with linux keywords and non-linux keywords, the results are shown in Figure 16-9.
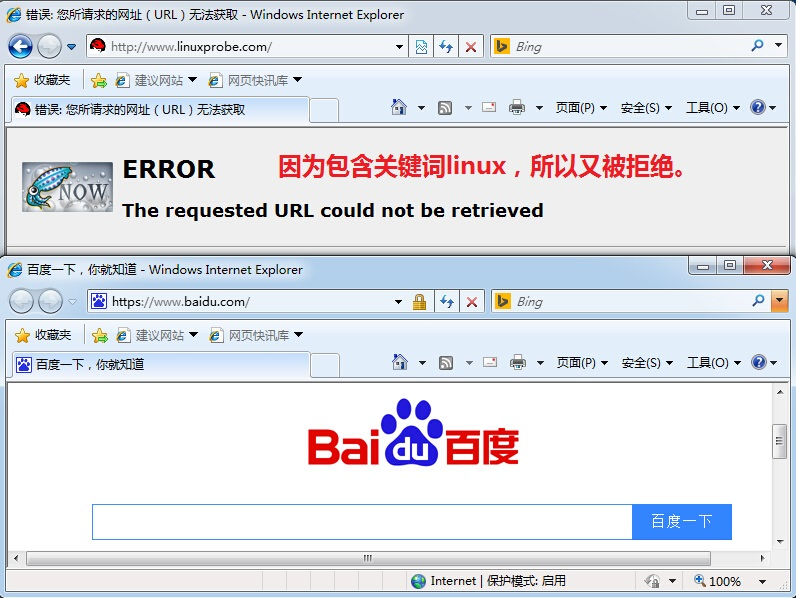
Figure 16-9 Presents results when clients visit websites with and without linux keywords, respectively
Lab 3: Prevent all clients from accessing a particular website.
In Experiment 2, because we prohibit all clients from accessing sites with linux keywords in their URLs, this will result in a large number of sites being missealed, affecting the normal work of colleagues. I n fact, by preventing clients from accessing a particular URL, you can avoid missealing. The Squid service program is configured and restarted according to the parameters shown below, and then tested, as shown in Figure 16-10.
[root@linuxprobe ~]# vim /etc/squid/squid.conf 24 acl Safe_ports port 777 # multiling http 25 acl CONNECT method CONNECT 26 acl deny_url url_regex http://www.linuxcool.com 27 # 28 # Recommended minimum Access Permission configuration: 29 # 30 # Deny requests to certain unsafe ports 31 http_access deny deny_url 33 http_access deny ! Safe_ports 34 [root@linuxprobe ~]# systemctl restart squid
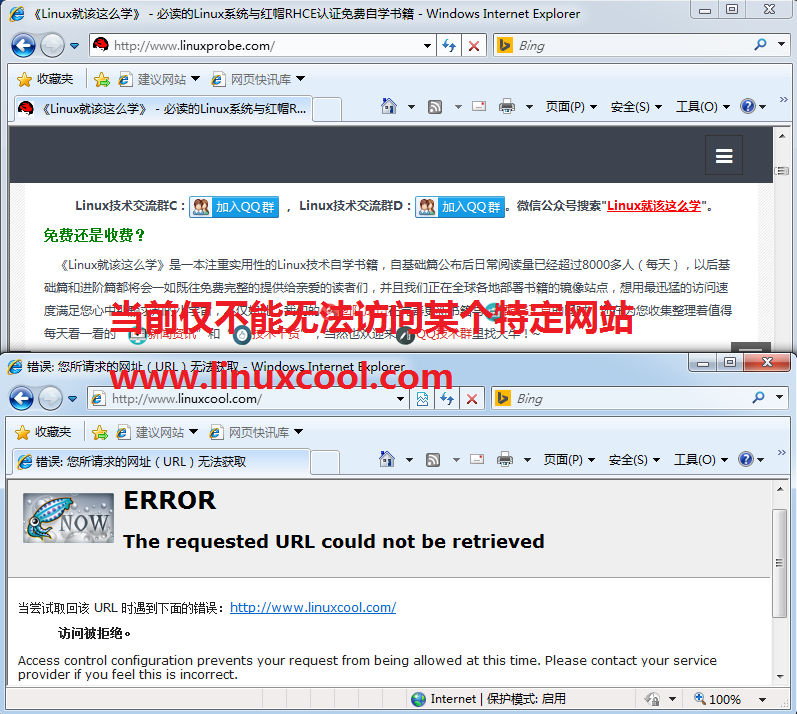
Figure 16-10 Cannot access this particular website using proxy services
Lab 4: Employees are prohibited from downloading files with certain suffixes within the corporate network.
In an enterprise network, a small percentage of people use the high-speed bandwidth of the corporate network to download resources privately (such as game installation files, movie files, etc.), which can affect the productivity of other colleagues. B y preventing all users from accessing .rar files such as .avi or files, you can prevent them from continuing to download resources and let them know. The Squid service program is configured and restarted according to the parameters shown below, and then tested, as shown in Figure 16-11.
If these employees are using P2P download software such as Thunderbolt to download resources, they can only use professional-grade application firewalls to prohibit them.
[root@linuxprobe ~]# vim /etc/squid/squid.conf 24 acl Safe_ports port 777 # multiling http 25 acl CONNECT method CONNECT 26 acl badfile urlpath_regex -i .mp3$ .rar$ 27 # 28 # Recommended minimum Access Permission configuration: 29 # 30 # Deny requests to certain unsafe ports 31 http_access deny badfile 33 http_access deny ! Safe_ports 34 [root@linuxprobe ~]# systemctl restart squid
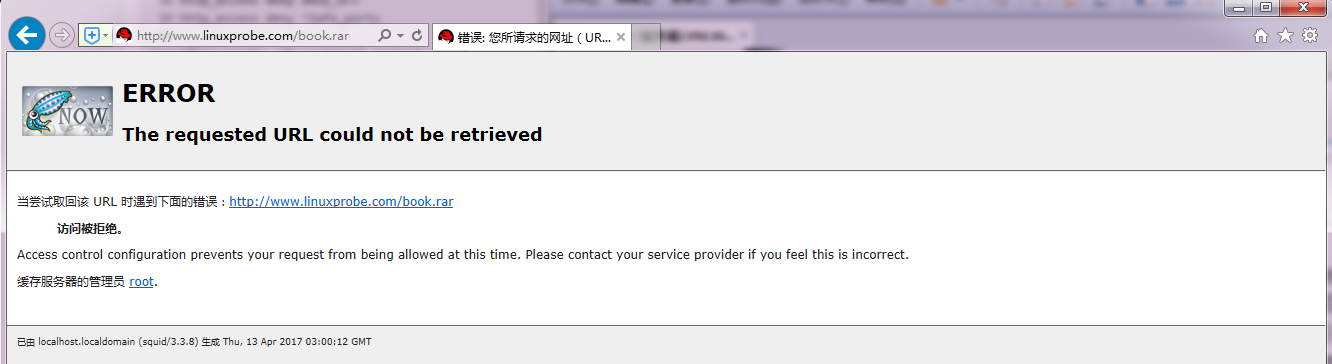
Figure 16-11 Cannot use the proxy service to download files with the specified suffix