Get to know the ELF files in Linux
Jun 01, 2021 Article blog
Table of contents
During the use of
Linux
systems, we often see the words
elf32-i386
ELF 64-bit LSB
etc.
So what exactly is
ELF
Several common ELF files
Under
Linux
the executables we generate after
gcc编译
belong to
ELF
file:
ELF
is a type of file, not a file specifically referred to as a suffix.
ELF
(Executable and Linkable Format, executable and linkable format) file format, under
Linux
there are three main types of files:
-
Executable (.out):
Executable Filewhich contains code and data, is a program that can run directly. Its code and data have fixed addresses (or offsets relative to base addresses) that the system can use to load programs into memory for execution.
-
Relocatable file (.o file):
Relocatable Filecontains the underlying code and data, but its code and data do not specify an absolute address, so it is suitable for linking to other target files to create executables or share target files.
-
Shared Target File (.so):
Shared Object Filealso known as a dynamic library file, contains code and data that is used at link time by linkersldand runtime dynamic linkersld.so.l、libc.so.l、ld-linux.so.l
ELF格式
can be structured roughly as:
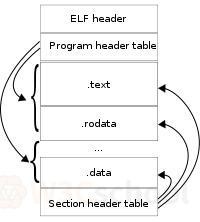
The ELF file consists of four parts:
ELF header
Program header table
the
Section
and the
Section header table
In fact, a file does not necessarily contain everything, and their location may not be arranged as shown, only the position of
ELF头
is fixed, the location of the rest of the part, size and other information is determined by the values in the
ELF头
Use of readelf tools
Under
Linux
we can use the
readelf
command tool to view some information about
ELF
file.
Let's start with a dynamic link related to demo:
File 1 (main.c):
include "test.h"
int main(void)
{
print_hello();
return 0;
}File 2 (test.c):
include "test.h"
void print_hello(void) { printf("hello world\n"); }
File 3 (test.h):
ifndef __TEST_H
#define __TEST_H
#include <stdio.h>
void print_hello(void);
#endif
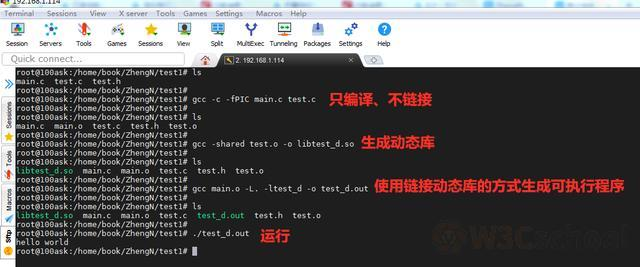
Execute the relevant commands to generate related files:
.out文件
.o文件
.so文件
as:
Let's use
readelf
command to see some information about these three types of files.
readelf
command format is:
readelf <option(s)> elf-file(s)
View executable header information:
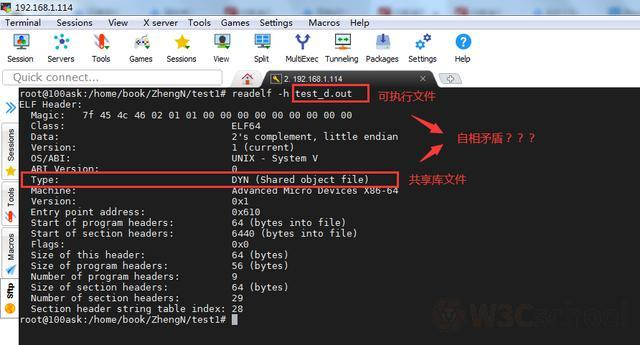
Looking at the executable header information, we find that the type in the header information is actually a shared library file, and we are looking at the executable file, paradoxically?
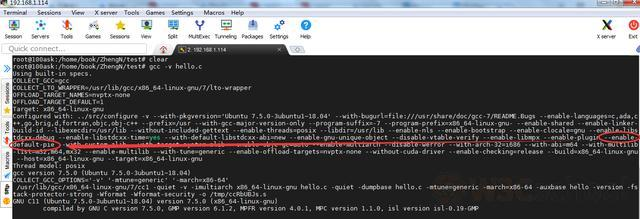
Check some information and find out:
gcc编译
default plus
--enable-default-pie
option:
Position-Independent-Executable
is a feature of
Binutils
glibc
and
gcc
that can be used to create code somewhere between a shared library and typically executable code - a program that can redistribute addresses like a shared library, which must be connected to
Scrt1.o
A
standard executable requires a fixed address, and the program can only execute correctly if it is mounted to that address.
PIE
enables the program to mount anywhere in the main memory like a shared library, which requires compiling the program into location-independent and linked to an
ELF
shared object.
PIE
was introduced because it allows programs to mount at random addresses, where the kernel typically runs at a fixed address, making it difficult for an attacker to carry out an attack with an executable code in the system if the location is not an option. A
ttacks such as buffer overflows cannot be implemented.
And the cost of this security upgrade is small.
In other words,
pie
is a means of protecting our executable programs.
Here we are just doing experiments, we can add
-no-pie
parameter first to turn off
pie
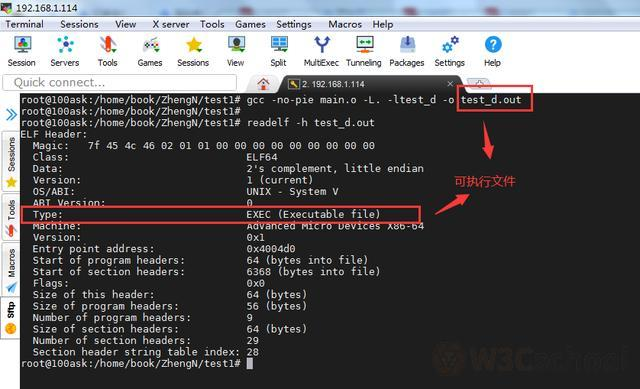
As you can see, the type is finally right.
ELF头部
information also contains information such as
Entry point address
Start of program headers
(the starting byte of the program
Start of section headers
(the starting byte of the header).
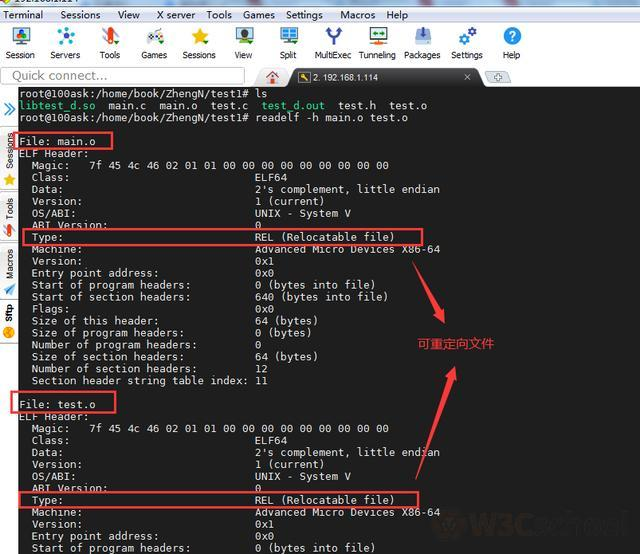
View repositionable file header information:
View shared target file header information:
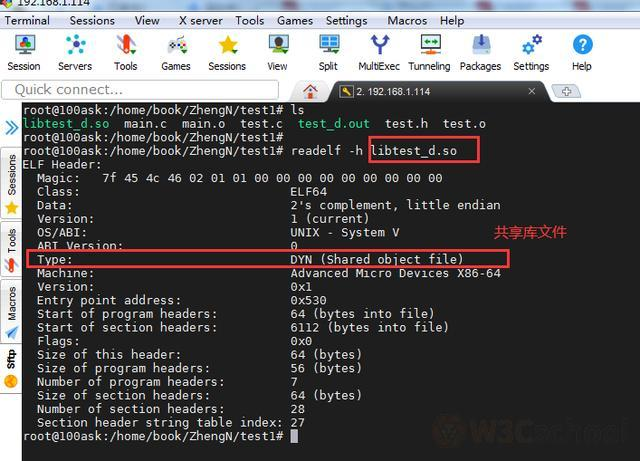
Similarly,
readelf
with other parameters allows you to view additional information about the
ELF文件
Use of the objdump tool
objdump
tool displays information for one or more target files.
objdump
command format:
objdump <option(s)> <file(s)>
Executables, relocatable files, and shared target files are all target files, so you can use this command to view some information.
View repositionable file disassembled information:
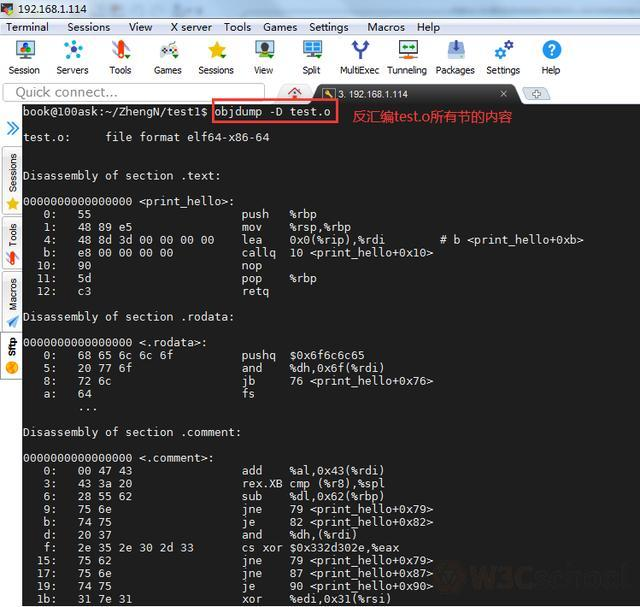
View executable disassembled information:
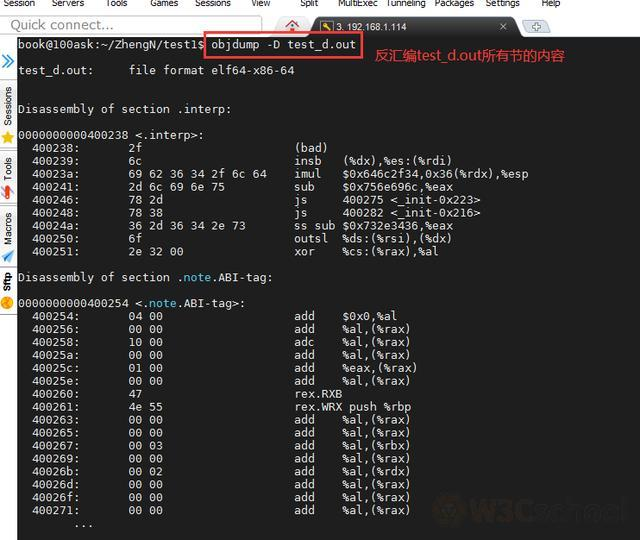
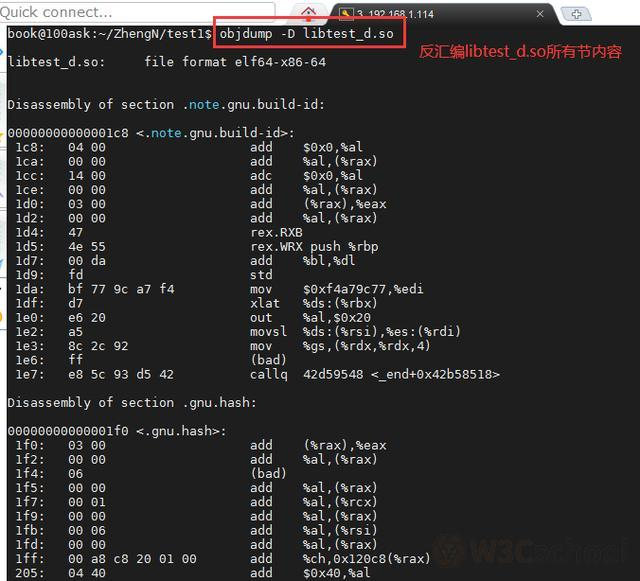
View shared target file disassembled information:
summary
That's the sharing. B
riefly introduces some information about
ELF
files, as well as two tools for analyzing
ELF
files.
ELF
file is a lot of content, and it's abstract, and it's a pit to analyze in detail. L
et's start with a simple understanding that I don't have the ability or the need to learn and analyze these underlying things, and then share them if we go deeper.
Interested students can learn with me
Linux tutorial: https://www.w3cschool.cn/linux/
Linux Microsyscope: https://www.w3cschool.cn/minicourse/play/linuxcourse
Linux should learn this: https://www.w3cschool.cn/linuxprobe/