10.4 Personal User Page feature
May 24, 2021 That's what Linux should learn
If you want to set up a separate site for each user in your system, the usual approach is to deploy multiple sites based on the virtual site hosting feature. B ut this work can be painful for administrators (especially when the number of users is large), and when users manage their own websites, they run into various permissions restrictions that require a lot of extra work. I n fact, the httpd service provider provides a personal home page function that is perfectly capable of this job. This feature allows all users in the system to manage their personal websites in their home directories, and it's easy to access.
Step 1: In the httpd service program, the personal page feature is not turned on by default. T o do this, we need to edit the following configuration file, and then add a hashtag before the UserDir disabled parameter on line 17 to indicate that the httpd service program has the personal user home page function turned on, and then remove the hashtag in front of the UserDir public_html parameter on line 24 (the UserDir parameter represents the name of the stored directory of the site data in the user's home directory, public_html Directory). Finally, remember to save after the modification is complete.
[root@linuxprobe ~]# vim /etc/httpd/conf.d/userdir.conf 1 # 2 # UserDir: The name of the directory that is appended onto a user's home 3 # directory if a ~user request is received. 4 # 5 # The path to the end user account 'public_html' directory must be 6 # accessible to the webserver userid. This usually means that ~userid 7 # must have permissions of 711, ~userid/public_html must have permissions 8 # of 755, and documents contained therein must be world-readable. 9 # Otherwise, the client will only receive a "403 Forbidden" message. 10 # 11 <IfModule mod_userdir.c> 12 # 13 # UserDir is disabled by default since it can confirm the presence 14 # of a username on the system (depending on home directory 15 # permissions). 16 # 17 # UserDir disabled 18 19 # 20 # To enable requests to /~user/ to serve the user's public_html 21 # directory, remove the "UserDir disabled" line above, and uncomment 22 # the following line instead: 23 # 24 UserDir public_html 25 </IfModule> 26 27 # 28 # Control access to UserDir directories. The following is an example 29 # for a site where these directories are restricted to read-only. 30 # 31 <Directory "/home/*/public_html"> 32 AllowOverride FileInfo AuthConfig Limit Indexes 33 Options MultiViews Indexes SymLinksIfOwnerMatch IncludesNoExec 34 Require method GET POST OPTIONS 35 </Directory> 第2步:在用户家目录中建立用于保存网站数据的目录及首页面文件。 In addition, you also need to modify the permissions of the home directory to 755, and ensure that others also have the authority to read the content inside.
[root@linuxprobe home]# su - linuxprobe Last login: Fri May 22 13:17:37 CST 2017 on :0 ( linuxprobe@linuxprobe. s.) mkdir public_html.linuxprobe@linuxprobe.) echo "This is linuxprobe's website" public_html/index.html (linuxprobe@linuxprobe-$ chmod -Rf 755 /home/linuxprobe Step 3: Restart the httpd service program, enter the URL in the browser's address bar, in the form of "URL/user name" (where the wave number is required, and there are no spaces between the URL, wave number, user name), theoretically you can see the user's personal website. U nsurprisingly, the system displays an error-reporting page, as shown in Figure 10-9. This must also be the scourge of SELinux.
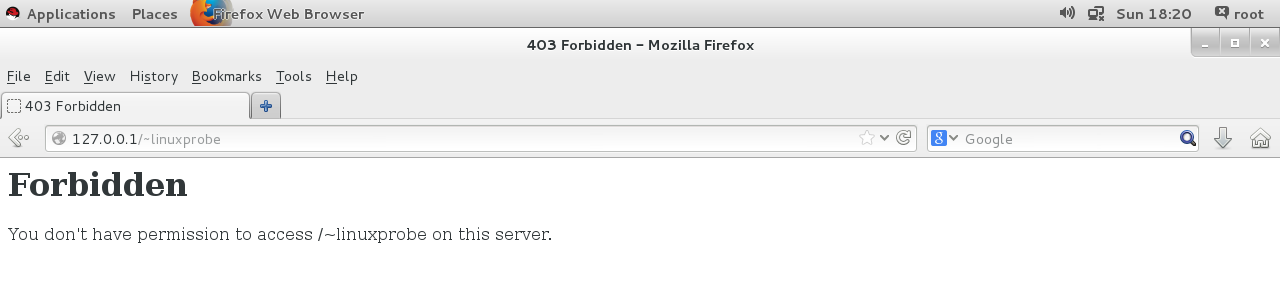
Figure 10-9 prohibits access to a user's personal website
Step 4: Think about what called the error this time. W hen the httpd service provider provides the function of a personal user's home page, the user's website data directory itself should be stored in the home directory corresponding to the user, so there should be no need to modify the SELinux security context of the home directory. H owever, the concept of the SELinux domain is also talked about earlier. T he SELinux domain ensures that the service program cannot perform illegal operations and can only provide services to the user on its part. Has this personal user page feature suddenly turned on in the httpd service been allowed by default by the SELinux domain?
Next, use the getsebool command to query and filter out all security policies related to the HTTP protocol. Where off is prohibited and on is allowed.
[root@linuxprobe ~]# getsebool -a | grep http httpd_anon_write --> off httpd_builtin_scripting --> on httpd_can_check_spam --> off httpd_can_connect_ftp --> off httpd_can_connect_ldap --> off httpd_can_connect_mythtv --> off httpd_can_connect_zabbix --> off httpd_can_network_connect --> off httpd_can_network_connect_cobbler --> off httpd_can_network_connect_db --> off httpd_can_network_memcache --> off httpd_can_network_relay --> off httpd_can_sendmail --> off httpd_ dbus_avahi --> off httpd_dbus_sssd --> off httpd_dontaudit_search_dirs --> off httpd_enable_cgi --> on httpd_enable_ftp_server --> off httpd_enable_homedirs --> off httpd_execmem --> off httpd_graceful_shutdown --> on httpd_manage_ipa --> off httpd_mod_auth_ntlm_winbind --> off httpd_mod_auth_pam --> off httpd_read_user_content --> off httpd_run_stickshift --> off httpd_serve_cobbler_files --> off httpd_setrlimit --> off httpd_ ssi_exec --> off httpd_sys_script_anon_write --> off httpd_tmp_exec --> off httpd_tty_comm --> off httpd_unified --> off httpd_use_cifs --> off httpd_use_fusefs --> o ff httpd_use_gpg --> off httpd_use_nfs --> off httpd_use_openstack --> off httpd_use_sasl --> off httpd_verify_dns --> off named_tcp_bind_http_port --> off prosody_ b ind_http_port --off faces so many SELinux domain security policy rules that it's really not necessary to understand them one by one, as long as we can roughly guess the relevant policy purpose by name. F or example, if you want to turn on the personal home page feature of the httpd service, should the SELinux domain security policy httpd_enable_homedirs used? W hen you're generally sure, you can use the setsebool command to modify the Boolean values of the rules in the SELinux policy. I t is important to remember to add the -P parameter after the setsebool command for the modified SELinux policy rules to take effect permanently and immediately. The page is then refreshed, as shown in Figure 10-10.
[root@linuxprobe ~]# setsebool -P httpd_enable_homedirs=on [root@linuxprobe ~]# firefox
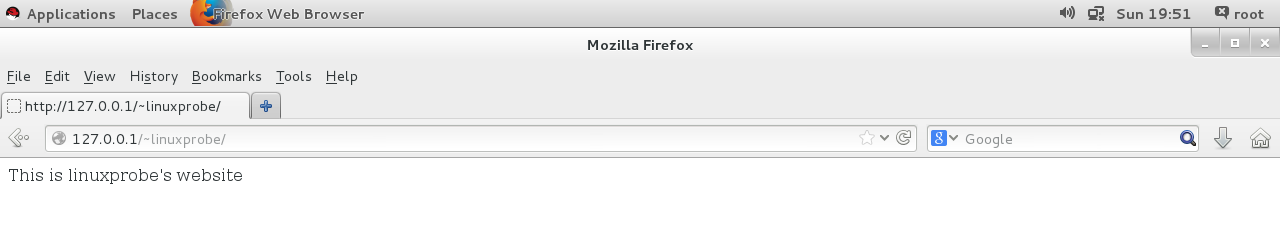
Figure 10-10 Normally see the content on the main page of an individual user
Sometimes, the owner of a Web site does not want to display the content of the page directly, but only wants authenticated visitors to see the content inside, so you can add a password function to the Site.
Step 1: Use the httpsswd command to generate a password database first. The -c parameter represents the first build, followed by the addition of the deposit file for the password database and the authentication of the user name to be used (the user does not have to be a local account already in the system).
root@linuxprobe htpasswd -c /etc/httpd/passwd linuxprobe New password: Enter the password for web verification here Re-type new password: enter again to confirm Add password for user linuxprobe Step 2: Edit the profile of the personal user's home page feature. T he parameter information of lines 31 to 35 is modified to the following, where the beginning of the hashtag is the comment information added by Mr. Liu Wei, which can be ignored. Then save and exit the profile and restart the httpd service program to take effect.
[root@linuxprobe ~]# vim /etc/httpd/conf.d/userdir.conf 27 # 28 # Control access to UserDir directories. T he following is an example 29 # for a site where these directories are restricted to read-only. 30 # 31 <Directory "/home/*/public_html"> 32 AllowOverride all
The password verification file just generated saves the path
33 authuserfile "/etc/httpd/passwd"#当用户尝试访问个人用户网站时的提示信息34 authname "My privately website"35 authtype basic#用户进行账户密码登录时需要验证的用户名称36 require user linuxprobe37 </Directory>[root@linuxprobe ~]# systemctl restart httpd
After that, when a user wants to visit a user's personal website again, they must enter an account and password to access it properly. I n addition, the account and password used for verification is a password password generated with the htpasswd command dedicated to website login, not the user password in the system, please do not get me wrong. The login interface is shown in Figure 10-11.
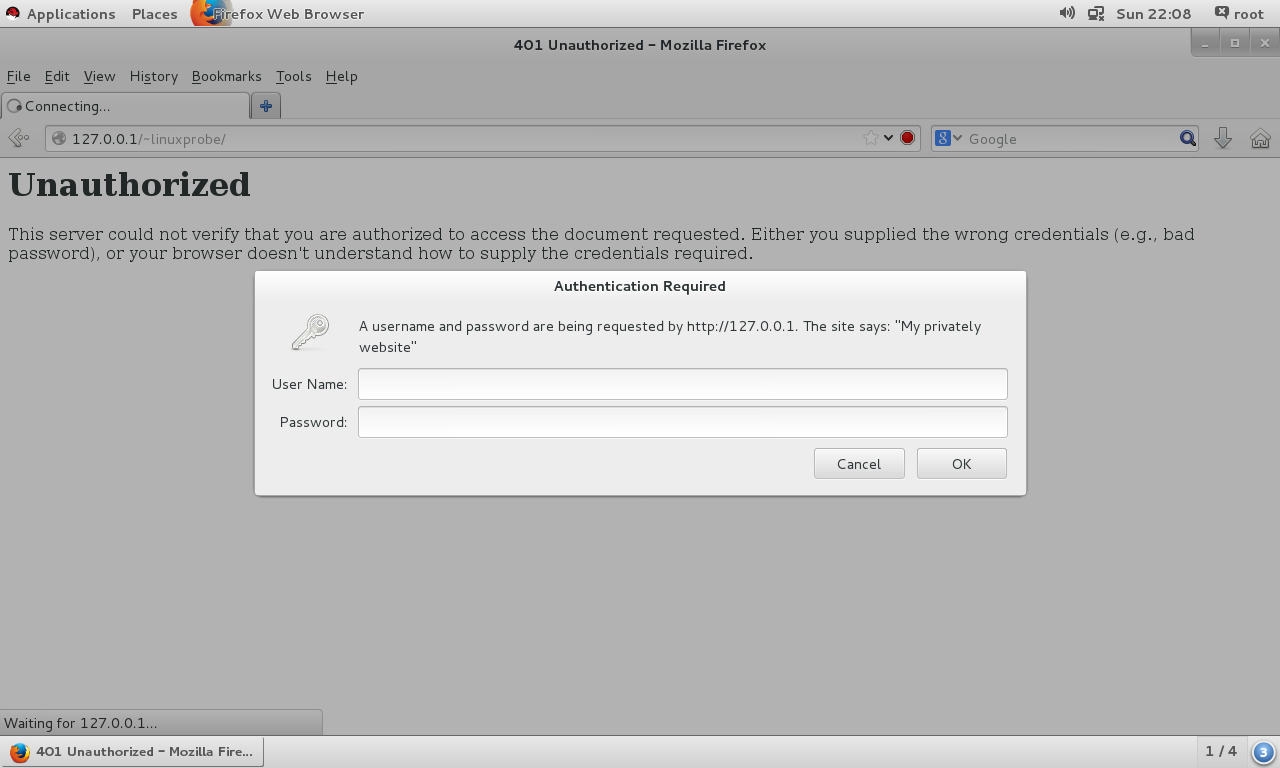
Figure 10-11 The website prompts that you need to enter your account number and password to access it
Have a problem? Ask bold questions!
Because readers have different hardware or operation errors may lead to experimental configuration errors, please be patient and take a closer look at the operation steps, do not be discouraged
Linux technical exchange please add Group A: 560843 (full), Group B: 340829 (recommended), Group C: 463590 (recommended), click here to view the national group.
This group features: through password verification to ensure that each group member is "Linux should learn" readers, more targeted, from time to time free to receive customized gifts.